Why manage technology Governance Risk and Compliance? And how?
Because to err is human, to really mess things up requires a computer. I am sure you have heard the Paul Ehrlich saying.
Now take it a step further, connect those computers. You now have a recipe for conditions that can go from zero to disaster, from blue skies to thunderstorms in the blink of an eye.
This is where we are. This is what we must protect. Managing the security of our information assets has come a long way. Just a few years back all it took was 5 questions on a spreadsheet, and now? If we factor what we must do, for whom, by when and who the enormity of the task reveals itself.
As I recently wrote, if we take a small 100-person organization, the numbers could look somewhat like this… 8 Domains. 150 Controls. 35,000 Recurring Tasks. 320K+ to-dos every year. 3.2M minutes. 6,750+ man days. 4 Full time employees – FTEs. 4% of the workforce.
To ensure that we do things correctly to keep our information assets and infrastructure secure we will have to manage these tasks effectively. This means figuring out what all needs to be done, plan for it, get those tasks by the right people, track and monitor their execution, and verify that they have been done correctly.
So, back to the question – Why manage technology Governance Risk and Compliance? Because a chain is only as strong as its weakest link. If we have 10,000 assets to protect and we do a great job with 99.99% coverage… that 1 asset that is left unprotected will cause all the grief.
I think this conclusively establish that technology governance needs our attention.
Let us now address the second question that is asked right in the beginning. How? How do we do all this for so many tasks? How do we set up to monitor a comprehensive GRC program?
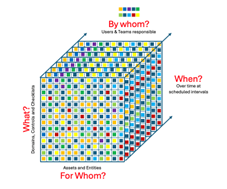
As we have seen – there are 4 principal dimensions along which we need to manage GRC programs – Controls, Time, Entities, People. Specifically, we need to ensure that we can manage…
All controls
GRC management programs need to have the capability to ensure that all the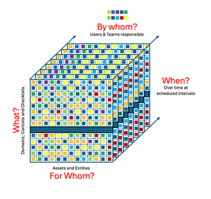 controls that need to be applied are being applied, over time, by all the teams that need to apply those controls, for all the assets that these controls need to be applied to.
controls that need to be applied are being applied, over time, by all the teams that need to apply those controls, for all the assets that these controls need to be applied to.
Failure to do so resulted in information of 147 million people being exposed at Equifax in 2017. This was attributed to failure to apply controls uniformly in the areas of vulnerability management, network security and access management.
Failures in controls related to 3rd party vendor management, Network management and Perimeter security resulted in the data breach at Target in 2013.
Over time
We can have a comprehensive program that across all controls, properly 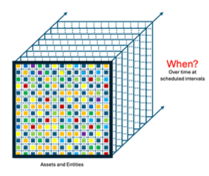 trained teams, and full coverage of assets that need to be secured, but if we do not apply these controls consistently over time it can lead to disasters.
trained teams, and full coverage of assets that need to be secured, but if we do not apply these controls consistently over time it can lead to disasters.
One of the more well-known cases was that of Capital One in 2019 where IT controls for access controls were not consistently applied leading to a loss of 100 million customer account data.
Does your GRC program ensure that access of users to assets like applications, systems, networks, facilities, devices, data stores is turned off when their role changes or when they leave the organization? If not, you may be setting yourself up to a situation like that at Capital One in 2019.
All assets
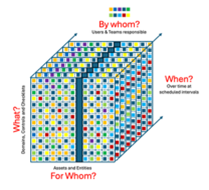 Yet again, we can have the most comprehensive GRC program with all the necessary controls, properly trained teams, being applied consistently over time, but if you miss out on some assets you open up a breach in your defenses and expose yourself to attacks.
Yet again, we can have the most comprehensive GRC program with all the necessary controls, properly trained teams, being applied consistently over time, but if you miss out on some assets you open up a breach in your defenses and expose yourself to attacks.
You just need to look at the DHS/CBP biometric data breach in 2019 when a device storing biometric facial recognition data was unencrypted and was hacked.
All concerned
We need to be able ensure that all that needs to be done for by a team, for all the controls, for all the assets, over time those that needs to be applied are being applied.
All that we have discussed is for nought if your team is not properly trained or prepared to handle your information assets. The most famous case that comes readily to mind is that at Snapchat in 2016 which happened because an employee clicked on a phishing email.
In conclusion we see that we need to manage our GRC program across all 4 dimensions – Controls, Time, People, Assets. Failure on any one of those dimensions can compromise the security of your information assets.
A chain is only as strong as its weakest link.





