Now that we’ve talked about what the ISO 27001 framework is all about and who actually needs it, let’s break it down a little more.
ISO 27001:2022 Annex A Structure & Controls
The 2022 version of the standard organizes 93 controls into four main themes:
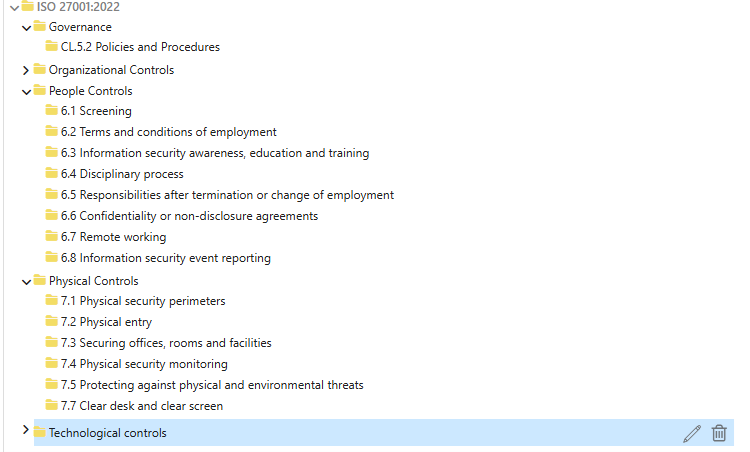
- Organisational Controls (Clause 5):37 controls
- People Controls (Clause 6):8 controls
- Physical Controls (Clause 7):14 controls
- Technological Controls (Clause 8):34 controls
Opening the standard and jumping straight to Annex A, can feel very confusing at first glance.
At the core of ISO 27001 are its controls—the specific security measures listed in Annex A that help an organization protect the confidentiality, integrity, and availability of information. These controls cover everything from policies and organizational structure to technical safeguards. When put together properly, they form the backbone of a strong Information Security Management System (ISMS).
The controls are written in a pretty high-level, generic way. If you read them as-is, you might think:
“Okay, I get what this is trying to say… but what exactly do I need to do to be compliant?”
That’s a very common reaction.
This is why, in practice, the first step is to translate those controls into actionable tasks. A simple way to start is by grouping them into practical domains as prescribed by ISO 27001:
Once you categorize them, the real work begins—turning those domains into actionable items that make sense for your organization. For example:
- Access management controls might mean setting up role-based access, enabling multi-factor authentication, and reviewing user permissions regularly.
- Technical controls like encryption become much easier to implement when you use the security features built into your cloud provider.
- Operational controls—like incident management—can be handled with a ticketing system, predefined workflows, and clear communication channels.
And then you have governance and policy controls, which are just as important. This is where you define your security policies, carry out regular risk assessments, document your procedures, and—equally critical—train your people.
Because, even with great technology, human error is still one of the biggest causes of security incidents.
In the end, ISO 27001 isn’t about checking boxes or impressing an auditor. It’s about building a culture of security. When you start implementing the controls gradually and weave them into your everyday operations, you’ll see how much they improve your security posture and overall resilience.
No matter how big or small your organization is today, having the right tool makes a huge difference in running a structured ISO 27001 program.
In the next post, we’ll look at what to expect from a good Technology GRC tool and how to approach ISO 27001 implementation in a simple, practical way.





